On July 25, to official micro-blog and the app said in a statement yesterday, recent user feedback account is fraudulent, multiple users to feedback their own easy-to-use vehicle stolen account, not only the account name had been tampered with, accounts in a short period also produced a number of large orders, payment information, account balance has been depleted.
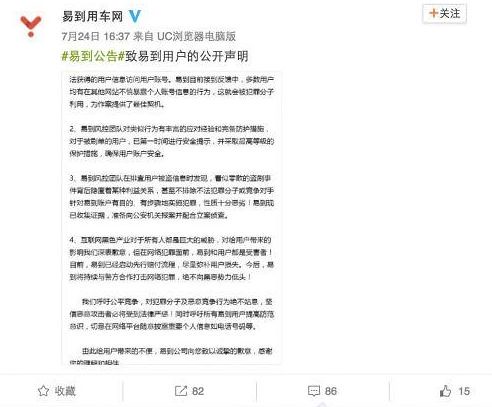
In a statement, said the company attaches, for users who are scalping, has safety tips for the first time, and to take the highest level of protection to ensure that the user account security. Also noted in the bulletin, to risk control team discovered during troubleshooting users stolen information, seemingly scattered incidents of fraudulent hiding behind some interest, even excluding criminals or rivals into account purposeful and systematic implementation of crime, is very bad. Easy to gather evidence going to the police and cooperate with investigation.
Currently, easy claim process has started, and try to make up for the losses incurred.


Uber have appeared before fraudulent events Vera Bradley cell phone case Vera Bradley iPhone cases
Not long ago, Uber news software vulnerability that causes the user account to be fraudulent. Uber China was responding to media, "said pilfer problem" is the common challenges to many Internet platforms, Uber network security team is investigating and will take strict security precautions.
Security firm TrendMicro has said for criminals, Uber, PayPal and even Netflix account has become much more than the credit card information of great value. According to the data of TrendMicro, Uber stolen account information in the underground market sells on average for each account $ 3.78, personally identifiable information are usually sold at between $ 1 and $ 3.30.
360 Mobile Guardian security experts analyze the recent taxi software using hot, fraudsters are targeting this market begin. Criminals by a significant spread of information on the Internet, luring users to take the bait, some criminals even well-made, hard to distinguish between the true and the false fish induced by site users, by way of counterfeit, such as customer service, providing fake software, such as deposit and pay the upgrade fee for swindling, users easily into the snare. These often hidden cell phone Trojan in fake software, sites, and users once you click Download, will result in the phone face Trojans and viruses, privacy theft, without deductions and other risks. Security expert tips online, online search services choose "official website" character certificate services Web page, when you download the software through official channels or security of third-party mobile applications download platforms, avoid the use of niche shopping platform.

No comments:
Post a Comment